Useful Info
RSSPosts: 33
Outlook for Android new feature – Add Contact !
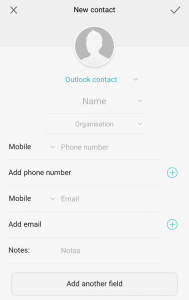 When I first switched to Android I couldn’t believe that the shiny Outlook app, which seemed pretty comprehensive and slick wasn’t actually able to add new contacts. Seemed a crazy omission. To make matters worse the Huawei P9 wasn’t able to sync new contacts to the Office 365 account either. They appeared to save but didn’t actually appear in the list. So no new contacts from my phone, which is probably when you need that feature the most.
When I first switched to Android I couldn’t believe that the shiny Outlook app, which seemed pretty comprehensive and slick wasn’t actually able to add new contacts. Seemed a crazy omission. To make matters worse the Huawei P9 wasn’t able to sync new contacts to the Office 365 account either. They appeared to save but didn’t actually appear in the list. So no new contacts from my phone, which is probably when you need that feature the most.
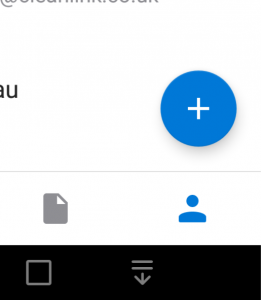 Anyway fast forward to 21 Aug 2017 and Outlook just updated to version 2.2.5 (221) mainline. I’ve never been so excited to see a little blue circular cross in the corner of the Contacts screen. My mobile life is transformed. New contacts, out and about, at last. Back to the future!
Anyway fast forward to 21 Aug 2017 and Outlook just updated to version 2.2.5 (221) mainline. I’ve never been so excited to see a little blue circular cross in the corner of the Contacts screen. My mobile life is transformed. New contacts, out and about, at last. Back to the future!
Here’s the link to the Outlook app.
PS Apple updated a short while ago with this feature
Subtle Gmail attack, look out for “data:text/html”
There’s a write-up at Wordfence about a subtle new type of attack via the Google Mail service. You receive an attachment that looks like its come from one of your contacts, possibly related to a shared interest or project. So your guard will be down.
![]()
At the top of your browser you can see https://accounts.google.com which sounds ok. However there’s a bit of extra info to the left, as you can see, saying “data:text/html”. That’s where the attack comes from and it triggers a sign-in page that looks like Google asking for your password again.
Delete the email, walk away!
Outlook junk filtering updates cease 1 Nov
 Microsoft have announced that from 1 Nov 2016, the junk mail definitions used by Outlook and Exchange to filter spam messages will no longer be updated. Filtering will still happen, it will just become less effective as time passes and the definitions aren’t updated to match what we see coming in via the internet.
Microsoft have announced that from 1 Nov 2016, the junk mail definitions used by Outlook and Exchange to filter spam messages will no longer be updated. Filtering will still happen, it will just become less effective as time passes and the definitions aren’t updated to match what we see coming in via the internet.
There’s a more detailed write-up at Slipstick but essentially, junk email campaigns are so short-lived now the definitions from Microsoft take too long to arrive at your computer or server (or you could be cynical and suggest MS are more interested in selling online accounts).
Fortunately we have a couple of very good solutions available to provide bolt-on email filtering to existing mailboxes and servers. Very little change is required to allow them to intercept your incoming email, filter the junk and then pass on to you, exactly as before (but without all the time-wasting spam).
 These cloud-based services are updated on-the-fly direct from the security teams, so are as reactive as possible. The advantage of an online system here is that it can see millions of email accounts and quickly spot spamming attempts, rapidly deploying blocks and cleaning up.
These cloud-based services are updated on-the-fly direct from the security teams, so are as reactive as possible. The advantage of an online system here is that it can see millions of email accounts and quickly spot spamming attempts, rapidly deploying blocks and cleaning up.
There are some useful additional services too – eg archiving, webmail, backup email service, etc. Please get in touch to discuss what we can help with. Costs are low, less than £1 a month – and can be a huge time-saver, as well as an additional security layer.
Has your email address been leaked ?
Mike recently presented at the Lets Do Business meeting, an independent not-for-profit business networking group. Probably the hottest topic in small business IT currently, is IT security. 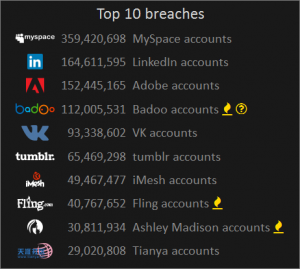 This presentation was a slight twist on the usual review of what you should be doing and how to implement layers of security for best protection.
This presentation was a slight twist on the usual review of what you should be doing and how to implement layers of security for best protection.
Instead, Mike took the group through some major data breaches, looking at what got hacked, how it happened and most importantly, what data leaked and what to do next if your email address appeared on the list.
Using the haveibeenpwned.com website came as a bit of surprise for some in the group, to discover their data was already out in the wild.
Read the write-up at the Lets Do Business blog. Don’t hesitate to call or email if you need help with these issues.
Windows 10 upgrade tips
With the Microsoft free upgrade offer for Windows 10 finishing in a few weeks, we’re seeing a lot of planned upgrade work for local businesses. Its better to plan the upgrade rather than rush straight in. Out list of tips will help ensure a more successful first-time upgrade.
- Check your key applications don’t have any known problems with Windows 10, eg Sage, ACT
- Upgrade to the latest drivers, especially for BIOS, video and network. We’ve seen plenty of old versions cause the upgrade to fail
- Upgrade your antivirus to the latest version (not just the definitions). Run a Malwarebytes scan
- Do a backup!
- Don’t start the upgrade 10 minutes before a 9am conference (yes we did get that phone call !)
- Once the upgrade has completed, check everything loads ok. Test your printers and scanners, we see quite a few that need a re-install.
Our favourite laptop mouse

Sometimes having just the right bit of equipment can make all the difference, especially something you use all day every day. Our favourite laptop mouse is the Microsoft Wireless Mobile Mouse 4000.

Little bit smaller than a standard desktop mouse, making it convenient for carrying. Compact wireless receiver which doesn’t get knocked off, if left in the laptop. Well placed ‘Back’ button, which is handy when researching on the internet. Standard AA battery which lasts ages. Good, smooth wheel, which doubles up as a third (middle) button. Make sure that middle button is configured to open a new tab when you click a link in your browser – that way you don’t lose the original page you’ve just come from.
Around £20 from Amazon http://amzn.to/24bdl8Q
Smarter email handling
There’s a lot you can do with Outlook email, whether its on your own server or Hosted Exchange like Office 365. (We can provide several flavours of both.)

It doesn’t have to be the simple option of one mailbox and one email address. You can add multiple email addresses to one copy of Outlook. Then add some rules to change how they process. For instance you might be responsible for emails sent to info@yourcompany and sales@yourcompany. For some of our clients we setup ‘info’ and ‘sales’ so that emails go into separate folders. Its still the same Outlook account, but it makes it a lot easier to process, plus you can identify priorities better, eg sales are a lot more important than info enquiries!
But why not flip that round, have a mailbox with one email address and multiple people, eg admin@ for processing the administration and then let all the admin team have access to it. As its one mailbox they can easily see which enquiries have been processed and which are outstanding. Maybe add a bit of colour coding to show enquiry status.
If you have a brochure request form on your website, send the request through to one of these accounts but route it into a subfolder. That way it can be left until later in the day or when someone has time, aiming to post the brochure requests all in one go just before the post is collected.
Outlook is about a lot more than just receiving emails, make sure its working efficiently for you.
Protect your WordPress website
We see a lot of attempted attacks against WordPress websites, due to its popularity and have also been called in when attacks have been successful. There are a number of measures that you can take to help protect yourself.
- Don’t use obvious usernames or passwords – they need to be difficult to guess. eg if your website is called Redleg IT then don’t make the username redleg !
- Make sure you have the Wordfence plugin running, it will block repeated failed logins – we see plenty of those from all over the world, particularly from the Ukraine at the moment. Wordfence has a lot of security features that are essential and its free (you just pay if you want the Premium features).
 Even though you’ve got obscure usernames, there is still something called an enumerated attack that is an attempt to break your password with a guess at a login ID of 1, or other obvious low number. The solution is a bit technical, but you can login to the MySQL database behind the scenes and run the commands described at www.wpwhitesecurity.com/wordpress-security/change-wordpress-administrator-id (Don’t hesitate to call if you want a hand with this)
Even though you’ve got obscure usernames, there is still something called an enumerated attack that is an attempt to break your password with a guess at a login ID of 1, or other obvious low number. The solution is a bit technical, but you can login to the MySQL database behind the scenes and run the commands described at www.wpwhitesecurity.com/wordpress-security/change-wordpress-administrator-id (Don’t hesitate to call if you want a hand with this)- Another important layer of security that you can add is CloudFlare. Again the basic service is free. They will attempt to mitigate any DDOS attacks or unusual connections that are detected, whilst maintaining a normal service for legitimate website visitors. If you come under attack, this service works almost like magic!
- Update, update, update – WordPress regularly issue security updates. Make sure you load those updates and the plugin updates ASAP. We do this as a matter of course for all our clients.
Common Passwords, Popular PINs
 Following on from our re-tweeted ‘Do Not Use These Passwords’ list, we now bring you the most popular 4 digit PIN codes list.
Following on from our re-tweeted ‘Do Not Use These Passwords’ list, we now bring you the most popular 4 digit PIN codes list.
DO NOT USE any of the entries on either of these lists, they’re so popular that its the first thing someone will guess at, to break into your account.
In fact looking at the percentages of how popular these are (eg 1234 is used 10% of the time!), we can work out how successful they will be at unlocking an iPhone.
You get 10 attempts at unlocking an iPhone, so using the top 10 PINs listed you’d be able to unlock every 5th iPhone you tried, on average.
That assumes the iPhone is locked with a 4 digit code – now that’s a great hint to immediately move to 6 digits, or better still characters, for your lock code … but whatever you do, don’t choose 123456 or 111111 !
Thanks to DataGenetics for the initial analysis, there’s a lot more detail in their blog.
How to fix a cryptovirus like Locky, Cryptolocker, Torrentlocker
 “Your Backup Plan never survives first contact with a cryptovirus”. Its the most likely security incident that will test how well thought out your backup strategy is.
“Your Backup Plan never survives first contact with a cryptovirus”. Its the most likely security incident that will test how well thought out your backup strategy is.
On 17th Feb at 2.07pm a receptionist opened an email attachment that looked like a legitimate invoice. At 2.08pm a download called eiaus11.exe arrived in the temp directory and launched. By 4pm it had encrypted nearly 91,000 files – all the Word documents, Excel documents, PowerPoint presentations, databases, images, x-rays, patient info. The ransom for the decrypt password was £300. That’s an absolute last resort – Don’t pay the ransom! You will go on a mailing list for a lot of future attacks.
Its almost not worth wasting the time trying to find a way round the encryption. Most of them are pretty slick now, hiding the decryption key somewhere on the internet, untraceable Bitcoin payment, even offering tech support. Just occasionally a fix turns up but months after the event.
The only other cure is to fire up the backup and restore to the previous evening. However some of the cryptoviruses are now targeting backups, in an effort to maximise ransom payment. Dropbox, Onedrive and similar file sync tools are not actually backups – encrypted files will be synchronised to the data centre and then to your mobile devices. Shadow file copy (a handy Windows file recovery mechanism) is deleted. A backup drive on a server that is shared will be attacked and encrypted.
Make sure your backup and security is multi-layered and comprehensive – on-site backup, off-site backup, email filtering, desktop anti-virus. Make sure its a full backup. Make sure it is tested regularly. You don’t want the first test to be when you’re staring at 91,000 inaccessible files with the business stopped dead in its tracks.
On the 18th Feb at 9.30am, the online backup completed the restore of the appointment database and all the related customer info. The receptionist logged back in and everyone breathed a sigh of relief, a little greyer, a little wiser.
The biggest issue encountered wasn’t the encryption or being unable to work, it was the fact that the broadband service was a limited package, with an almost used up allowance that wouldn’t allow for a full download from the backup service. As they say, your plan never survives first contact with the enemy. Use our experience to revise your plan.